By using Access Map, teams can:
- Validate policies before deployment.
- Detect misconfigurations and over-permissions.
- Simplify compliance audits.
- Continuously monitor effective access.
How to navigate to Access Map
To open Access Map:- Navigate to Policy Store (e.g., PetStore).
- Click on the Policies tab.
- Click on the Access Map button located next to the Edit button.

Query Policies for Governance
Query Access Map: What access does John have?
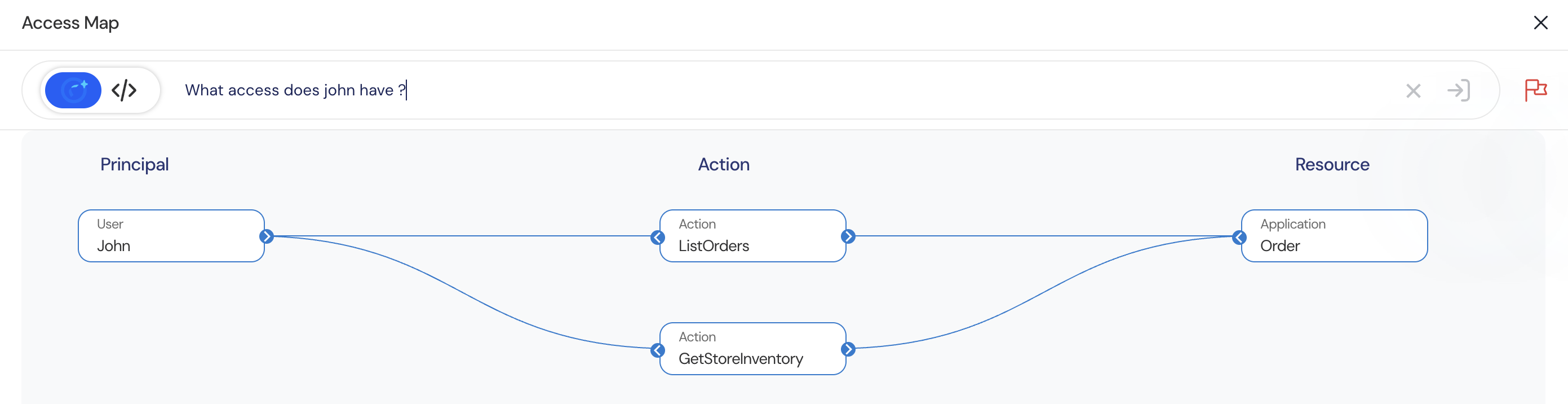
| Access | Principal | Action | Resource |
|---|---|---|---|
| Permit | User::John | ListOrders, GetStoreInventory | Application::Order |
Benefits of Access Map
| Benefit | Description |
|---|---|
| Full Visibility | View actual access granted by active policies. |
| Policy Simulation | Evaluate changes in a simulated environment before applying them to production. |
| Misconfiguration Detection | Instantly identify unintended access paths and over-provisioned users. |
| Compliance Audit Support | Generate visual evidence of access relationships for governance reports. |
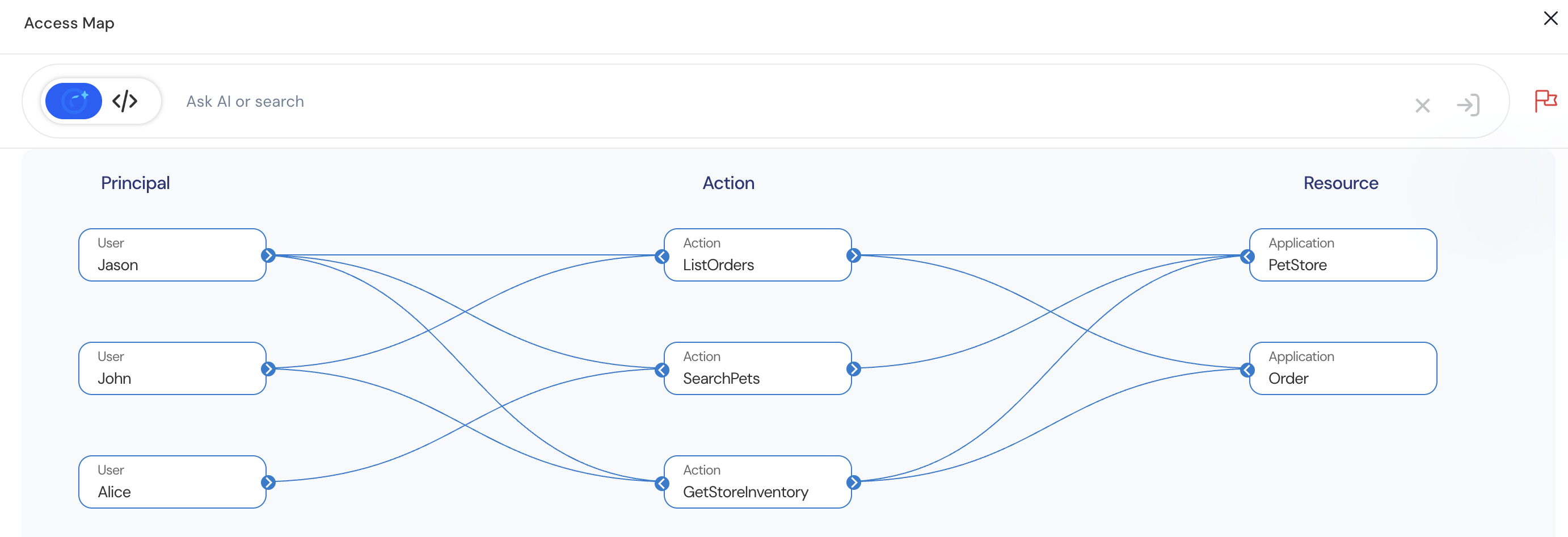
Access Map Elements
| Component | Description |
|---|---|
| Principal Nodes | Represent users, roles, or groups. |
| Resource Nodes | Represent the resources or objects governed by the policy. |
| Actions | Operations permitted on each resource. |
Governance Best Practices
- Perform regular Access Map reviews for critical applications.
- Use simulations prior to publishing any policy changes.
- Include Access Map outputs in governance documentation.
- Integrate Access Map analysis into quarterly security reviews.
With Access Map, Reva simplifies policy governance by combining visibility, validation, and compliance into one actionable interface.

